Can You File For Divorce Via Facebook Messenger?




There is legit science to quantum theory but misinterpretations justify an assortment of pseudoscience. Let’s examine why.
Quantum science isn’t a young science anymore. This year, 2015, the term “quantum”, as it relates to quantum physics, turns 113 years old. The term as we know it first appeared “in a 1902 article on the photoelectric effect by Philipp Lenard, who credited Hermann von Helmholtz for using the word in reference to electricity”(Wikipedia). During it’s first century of life attempts to understand quantum particle behavior have lead to a bunch of discoveries. Quantum physics has furthered understanding of key physical aspects of the universe. That complex understanding has been used to develop new technologies.
Quantum physics is enigmatic in that it pushes the limits of conceptualization itself, leaving it seemingly open to interpretation. While it is has been used to predict findings and improve human understanding, It’s also been used by charlatans who have a shaky-at-best understanding of science. Quantum physics has been misappropriated to support a bunch of downright unscientific ideas.
It’s easy to see why it can be misunderstood by well-intentioned people and foisted upon an unsuspecting public by new age hacks. The best minds in academia don’t always agree on secondary implications of quantum physics. No one has squared quantum theory with the theory of relativity, for example.
Most people are not smart enough to parse all the available research on quantum physics. The public’s research skills are notoriously flawed on any subject. The internet is rife with misinformation pitting researchers against their own lack of critical thinking skills. Anti-science and pseudoscience alike get a surprising amount of traction online, with Americans believing in a wide variety of superstitions and erroneous claims.
In addition to the public simply misinterpreting or misunderstanding the science, there is money to be made in taking advantage of gullible people. Here are some false claims that have erroneously used quantum theory as supporting evidence:
The internet loves this one. Contemporary multiple universe theor ies are philosophy, not science, but that didn’t stop Australian physicists Howard Wiseman and Dr. Michael Hall from collaborating with UC Davis mathematician Dr. Dirk-Andre Deckert to publish the “many interacting worlds” theory as legit science in the otherwise respectable journal, Physical Review X. This is the latest in a train of thought that forgoes scientific reliance on evidence and simply supposes the existence of other universes, taking it a step further by insisting we live in an actual multiverse, with alternate universes constantly influence each other. Um, that’s awesome but it’s not science. You can read their interpretation of reality for yourself.
ies are philosophy, not science, but that didn’t stop Australian physicists Howard Wiseman and Dr. Michael Hall from collaborating with UC Davis mathematician Dr. Dirk-Andre Deckert to publish the “many interacting worlds” theory as legit science in the otherwise respectable journal, Physical Review X. This is the latest in a train of thought that forgoes scientific reliance on evidence and simply supposes the existence of other universes, taking it a step further by insisting we live in an actual multiverse, with alternate universes constantly influence each other. Um, that’s awesome but it’s not science. You can read their interpretation of reality for yourself.
Deepak Chopra is a celebrated new age guru whose views on the human condition and spirituality are respected by large numbers of the uneducated. By misinterpreting quantum physics he has made a career of stitching together a nonsensical belief system from disjointed but seemingly actual science. Chopra’s false claims can seem very true when first investigated but has explained key details that Chopra nonetheless considers mysterious.
‘The Power’ and ‘The Secret’ are best-selling books that claim science supports what can be interpreted as an almost maniacal selfishness. The New York Times once described the books as “larded with references to magnets, energy and quantum mechanics.” 
The Secret’s author, Rhonda Byrne, uses confusing metaphysics not rooted in any known or current study of consciousness by borrowing heavily from important-sounding terminology found in psychology and neuroscience. Byrne’s pseudoscientific jargon is surprisingly readable and comforting but that doesn’t make the science behind it any less bogus.

There isn’t anything in quantum physics implying a solipsism or subjective experience of reality but that doesn’t stop Scientology from pretending we each have our own “reality” – and yours is broken.
Then there is the oft-headlining, almost post modern psuedoscientific masterpiece of utter bullshit: Scientology.
Scientology uses this same type of claim to control it’s cult following. Scientology relies on a re-fabrication of the conventional vocabulary normal, English-speaking people use. The religion drastically redefined the word reality. L.R. Hubbard called reality the “agreement.” Scientologists believe the universe is a construct of the spiritual beings living within it. The real world we all share is, to them, a product of consensus. Scientology describes, for example, mentally ill people as those who no longer accept an “agreed upon apparency” that has been “mocked up” by we spiritual beings, to use their reinvented terminology. Scientologists misuse of the word reality to ask humans, “what’s your reality?” There isn’t anything in quantum physics implying a solipsism or subjective experience of reality but that doesn’t stop Scientology.
The struggle to connect quantum physics to spirituality is a humorous metaphor for subjectivity itself.
If you find yourself curious to learn more about quantum theory you should read up and keep and open mind, no doubt. The nature of a mystery is that it hasn’t been explained. Whatever evidence that might be able to help humanity understand the way reality is constructed is not going to come from religion or superstition, it will come from science. Regardless of the claims to the contrary, quantum theory only points out a gap in understanding and doesn’t explain anything about existence, consciousness or subjective reality.
|
Jonathan Howard
Jonathan is a freelance writer living in Brooklyn, NY |



After the rocky road of the test-based accountability era, the next stage of education reform seemed to promise a smoother ride. In 2010 the Common Core State Standards (CCSS), which set off high expectations for student academic performance in mathematics and English language arts, were adopted in 45 of the 50 states with strong bi-partisan support.
Since then, however, public approval of the CCSS has both declined and become more divisive. The Common Core is now at the epicenter of a heated political debate, with social media as one of the battlefields. There are upwards of 40,000 tweets using #commoncore each month right up to the present.
Although public discussions of education reform are part of America’s rich democratic history, their spillover into social media, on this scale, is unprecedented.
For the first time, education policy is playing out online as much as it is in professional corridors.
To examine the CCSS debate on Twitter, my colleagues Alan Daly from the University of California, San Diego and Miguel Del Fresno from The National University of Distance Education (UNED) in Madrid, Spain, and I collected almost 190,000 tweets from 53,000 people using the twitter hashtag #commoncore for six months from September 2013 through February 2014.
This period covered the key time when national support for the CCSS was declining and partisanship was rising. Our methods and results are reported on an interactive multi-media website: www.hashtagcommoncore.com
Here are a few highlights of what we found:
First, our analysis of the social network using #commoncore revealed the emergence of three distinct sub-communities.

The #Commoncore Project, Author provided
One group was largely made up of CCSS supporters; another distinct group was made up of individuals largely from within the education sector who opposed the CCSS. The final, and largest group, was made up of individuals and groups from outside of education who opposed the CCSS.
Second, we found the CCSS debate was really a proxy war over broader cultural disagreements on the future direction of American education.
Interestingly,very few tweets were about the standards themselves. Most were focused on other education issues that the standards have come to represent.
These included:
Opposition to a federal role in education.
A belief that the CCSS provide access to data on children that can be used for exploitative purposes.
A source for over-testing children.
A way for business interests to exploit public education for private gains.
A belief that an emphasis on standards distracts from the deeper underlying causes of low educational performance, including poverty and social inequity.
Third, in a deeper analysis of the language of the tweets themselves, we noticed two dominant rhetorical approaches. One used more rational, analytical language, which we dubbed “policyspeak”. The other approach we called “politicalspeak” as it employed more emotional language. We found that supporters of the CCSS were more likely to use the policyspeak language, while opponents were more likely to use politicalspeak. These approaches most likely were meant to appeal to different audiences.

The #Commoncore Project, Author provided
Significantly, there was strong media presence in the #commoncore network and evidence that the topics and messages were transported from this space into the mainstream media.
We believe this study shines new light on how social media-enabled social networks are changing the dynamics of a political environment in which public policy is formulated.
While it may seem that social media and the internet have been ever present, consider that the last major federal education policy initiative, the No Child Left Behind (NCLB) Act of 2001 was enacted three years before Facebook was first liked; four years prior to the first YouTube video, and five years before the first tweet on Twitter.
We believe, for the first time, a new “activist public” are jockeying with more traditional advocacy groups through the social media for attention in the policy arena.
Related to this is how media has evolved over the last half century: first from a passive system dominated by a few central opinion-makers; then to a splintered proliferation of more partisan media outlets; and now into a more active phase of social media in which we are the media, where individuals are not just the consumers but producers and perpetuators of what is news and dominant opinion.
Finally, these analyses are a reminder that we live in a social world in which our understanding is derived from a complex set of interdependent social processes in which the diffusion of ideas, beliefs and opinions are stretched across individuals and multiple levels of an inter-related system.
![]()
This article was originally published on The Conversation.
Read the original article.

What has been so frustrating throughout the metadata “debate” is that we have been kept in ignorance as to what it was that the law enforcement agencies actually wanted to retain.
Now, at long last we finally find out, but unfortunately it is too late to discuss what should or should not be collected. The legislation, finally presented to parliament, has been agreed to by the federal opposition, so will become law.
Consequently, all we can do is look at what the legislation contains and see what we are now committed to. The metadata to be collected appears to match quite closely that released or leaked in earlier documents.
On the positive side, the actual metadata items to be collected have been written into the act rather than specified in regulations, giving parliament more control over what is collected than was originally proposed.
There is a provision for the Attorney-General to include items temporarily, but only for up to 40 parliamentary sitting days. There are also stronger restrictions on the agencies that can access metadata.
Also, there is to be some protection for journalists and their sources through a Public Interest Advocate.
Unfortunately, after that, there’s not a lot to be happy about.
It is now confirmed that this is going to be a substantial undertaking involving much more than storing a few system log files. There will be a great deal of data collected as to what we do online.
Email, social media and chat services are all explicitly mentioned in the legislation. This is unlikely to be a low cost exercise.
Adding to the cost will be the need for strong security of metadata storage. Stores of metadata are likely to be attractive targets for hackers, a fact recognised in the legislation, which requires the stored data to be encrypted. Unfortunately, security involves more than just encrypting stored data.
Added security costs may come from the need for physical security, security of data in transit, personnel security and the like. There is provision in the legislation for the Commonwealth to provide financial assistance, but it is not clear how much of the cost will be passed on to the consumer.
Looking at individual items, there is much to be worried about. Email addresses we communicate with and our use of social media and chat services, if disclosed, could all potentially affect our privacy.
Also it seems that location data of mobile devices is to be included. It will not be quite as bad as continuous monitoring of location, but metadata associated with mobile phone use will include the base station or WiFi hotspot that it was connected to at the start of the communication.
Another concern is that Item 5 lists “data volume usage” as an example of the type of data to be collected. It is difficult to understand why this is in the legislation other than as a mechanism for policing possible copyright infringement.
So, will this be worth it? Will the risk to privacy and the cost of implementing this scheme make us safer?
The law enforcement agencies presumably think so, but it is hard to understand why. Anyone with any technical understanding would be able to avoid much of the collection.
For example, collection of email addresses communicated with can be avoided by simply using an email provider not based in Australia who encrypts their communications.
Free WiFi services that do not ask for registration will also enable users to avoid many of the provisions. TOR, VLANs and Wickr provide other options for making metadata collection difficult.
There are quite a few questions as to why and whether we should be doing data retention. Sadly, it is too late for that.
![]()
This article was originally published on The Conversation.
Read the original article.

How would you feel if someone posted nude or explicit photos of you online? How about if they were posted by a former partner following a separation? Most people would be understandably mortified.
Few, if any, other form of privacy violations can be as hurtful and embarrassing as “revenge porn”. Consequently, society must act decisively in addressing this issue.
Yet until recently there was little one could do to prevent a former partner from posting compromising images or videos online, or to take them down once they’re released into the wild via social media.
But that’s starting to change. Social media sites such as Facebook, Twitter and Reddit, are beginning to take a much sterner stance against revenge porn, and the law is also starting to catch up.
Revenge porn has often been bundled with other forms of “sexting”. However, there are significant distinctions between consensual sexting and revenge porn. While sexting has been discussed extensively in legal literature and been the object of several law reform reports, revenge porn is now emerging as a distinct issue.
From a technical perspective, revenge porn requires two things:
The means to capture images/video, and
The means to distribute those materials.
Given that just about everyone has a good quality camera in their mobile phone or tablet and an internet connection these days, it is no wonder that these conditions are easily met. Or that revenge porn has become a major issue today.
Things have changed considerably since what appears to be Australia’s first revenge porn case Giller v Procopets. Here, a man had filmed his sexual activities with his partner at the time. When the their relationship deteriorated, the man showed the video tape to some people, and attempted, and threatened, to show it to others. On appeal to the Court of Appeal, the victim was awarded A$40,000 for injury to feelings as a result of the breach of confidence.
As with most, if not all, technology-related problem-areas, we need to turn to what I call the holy trinity of “reg”, “tech”, and “ed” –- we need regulation, technological solutions and education. Here I want to focus on some recent developments in the private sector as well as legal regulation of revenge porn.

Summer Skyes 11/Flickr, CC BY
For victims of revenge porn, the removal of the materials is of course a priority. For this reason, the cooperation of the platforms on which revenge porn is posted is of fundamental importance. Indeed, the power of the social media platforms is such that they can in some cases actually prevent the posting in the first place. It is therefore frustrating when decisions by social media organisations to block or allow content are opaque and inconsistent.
However, several social media sites are now working to improve their processes and clarify their practises. For example, as of last week Twitter now makes clear that:
You may not post intimate photos or videos that were taken or distributed without the subject’s consent.
And on March 16, 2015, Facebook announced new “Community Standards” to govern the conduct of its 1.39 billion users. The policy specifically addresses revenge porn:
To protect victims and survivors, we also remove photographs or videos depicting incidents of sexual violence and images shared in revenge or without permissions from the people in the images.
Our definition of sexual exploitation includes solicitation of sexual material, any sexual content involving minors, threats to share intimate images, and offers of sexual services. Where appropriate, we refer this content to law enforcement.
This is an important step, and follows a recent announcement by social media site Reddit that it has banned non-consentual nude photos shared on its site.
The law is also starting to react to revenge porn. As was reported in February, police and prosecutors in the UK are now equipped with a new criminal offence in order to tackle revenge porn. Canada, Japan and Israel are also working on legislation.
And in the US, for example, a man from San Diego was convicted in a case involving the running of a revenge porn website. There are also dozens of US states joining the push to crack down on revenge porn.
One contentious issue is what level of compensation courts should award in revenge porn cases. This issue was brought into the limelight in a judgement handed down by the Supreme Court of Sweden (in Sweedish). The Court awarded 76,000 kroner (~A$11,500) in compensation. The Supreme Court thereby more than doubled the compensation awarded by a much criticised decision by a lower court. That lower court had justified a lower amount of compensation by reference to the fact that a strong degree of openness about sexuality was now accepted in the contemporary ethical and social standards of a large section of the public.
This appears to be an example of an older generation misreading the social standards of a younger generation. Privacy –- not least in the sense of self-determination –- still matters, not least when it comes to matters such as sexuality.
And it seems both social media companies and the law are starting to catch up and deal with revenge porn.
![]()
This article was originally published on The Conversation.
Read the original article.

While Microsoft works on the final touches of its new browser, it confirmed that the brand “Internet Explorer” is officially over. Meanwhile, in the rest of the world, people rejoice with the thought of never having to deal with a terribly buggy and incompatible internet browser again, only to inevitably find out that it most likely will still remain as part of Microsoft’s operating system with a new name, currently running under the guise of Project Spartan at the Microsoft office.
In somewhat of a marketing gaffe, Chris Capossela, chief of marketing at Microsoft, said, “We’re now researching what the new brand, or the new name, for our browser should be in Windows 10. We’ll continue to have Internet Explorer, but we’ll also have a new browser called Project Spartan, which is codenamed Project Spartan. We have to name the thing.” So, in an effort to name the thing, they came up with a name, that also has a codename, and also doesn’t have a name, so they’re still trying to think of a name.
According to inside buzz, Microsoft is dropping the “Internet Explorer” brand due to its consistent poor reputation as a slow and buggy browser, despite the fact that even the latest versions have many built in, obvious design flaws such as not being entirely HTML, CSS and JavaScript compliant and being built into the operating system, making it a huge security risk that’s been exploited time and time again (and still to this day).
Each time the computer giant releases a new browser version, its consumers stupidly believe that it’ll be better than the last one, but soon run into problems with security, page rendering and functionality, and memory hogging causing system lags and crashes. The company blames the user and the world wide web for being a hostile environment while creating native scripting languages that offer a plethora of exploits to malicious coders and script kiddies. The end result is a poor user experience and lack of control over the software and the user’s interaction with the web. It doesn’t take an engineer to see this in action, just use the browser for a little while and you’ll see what happens to your computer.
While Microsoft works on coming up with another new name, despite the fact that they have one, they might want to think about the level of non-importance the name of a browser is when running under the “Microsoft” brand and work on creating a superior product which may actually be the real selling point overall.
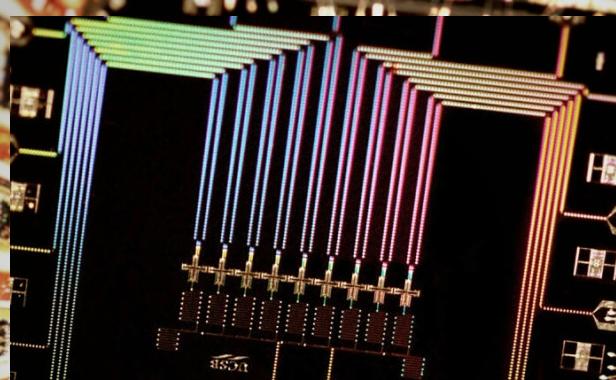
Quantum memory promises speed combined with energy efficiency. If made viable it will be used in phones, laptops and other devices and give us all faster, more trustworthy tech which will require less power to operate. Before we see it applied, the hardware requires redundant memory cells to check and double-check it’s own errors.
All indications show quantum tech is poised to usher the next round of truly revolutionary devices but first, scientists must solve the problem of the memory cells saving the wrong answer. Quantum physicists must redesign circuitry that exploits quantum behavior. The current memory cell is called a Qubit. The Qubit takes advantage of quantum mechanics to transfer data at an almost instantaneous rate, but the data is sometimes corrupted with errors. The Qubit is vulnerable to errors because it is physically sensitive to small changes in the environment it physically exists in. It’s been difficult to solve this problem because it is a hardware issue, not a software design issue. UC Santa Barbara’s physics professor John Martinis’ lab is dedicated to finding a workaround that can move forward without tackling the actual errors. They are working on a self-correcting Qubit.
The latest design they’ve developed at Martinis’ Lab is quantum circuitry that repeatedly self-checks for errors and suppresses the statistical mistake. Saving data to mutliple Qubits and empowering the overall system with that kind of desirable reliability we’ve come to expect from non-quantum digital computers. Since an error-free Qubit seemed last week to be a difficult hurdle, this new breakthrough seems to mean we are amazingly close to a far-reaching breakthrough.
Julian Kelly is a grad student and co-lead author published in Nature Journal:
“One of the biggest challenges in quantum computing is that qubits are inherently faulty so if you store some information in them, they’ll forget it.”
Last week I wrote about a hardware design problem called bit flipping, where a classic, non-quantum computer has this same problem of unreliable data. In effort to make a smaller DRAM chip, designers created an environment where the field around one bit storage location could be strong enough to actually change the value of the bit storage location next to it. You can read about that design flaw and the hackers who proved it could be exploited to gain system admin privileges in otherwise secure servers, here.
Bit flipping also applies to this issue in quantum computing. Quantum computers don’t just save information in binary(“yes/no”, or “true/false”) positions. Qubits can be in any or even all positions at once, because they are storing value in multiple dimensions. It’s called “superpositioning,” and it’s the very reason why quantum computers have the kind of computational prowess they do, but ironically this characteristic also makes Qubits prone to bit flipping. Just being around atoms and energy transference is enough to create unstable environments and thus unreliable for data storage.
“It’s hard to process information if it disappears.” ~ Julian Kelly.
Along with Rami Barends, staff scientist Austin Fowler and others in the Martinis Group, Julian Kelly is making a data storage scheme where several qubits work in conjunction to redundantly preserve information. Information is stored across several qubits in a chip that is hard-wired to also check of the odd-man-out error. So, while each Qubit is unreliable, the chip itself can be trusted to store data for longer and with less, hopefully, no errors.
It isn’t a new idea but this is the first time it’s been applied. The device they designed is small, in terms of data storage, but it works as designed. It corrects its own errors. The vision we all have of a working quantum computer able to process a sick amount of data in an impressively short time? That will require something in the neighborhood of a hundred million Qubits and each of the Qubits will be redundantly self-checking to prevent errors.
Austin Fowler spoke to Phys.org about the firmware embedded in this new quantum error detection system, calling it surface code. It relies on the measurement of change between a duplication and the original bit, as opposed to simlpy comparing a copy of the same info. This measurement of change instead of comparison of duplicates is called parity recognition, and it is unique to quantum data storage. The original info being preserved in the Qubits is actually unobserved, which is a key aspect of quantum data.
“You can’t measure a quantum state, and expect it to still be quantum,” explained Barends.
As in any discussion of quantum physics, the act of observation has the power to change the value of the bit. In order to truly duplicate the data the way classical computing does in error detection, the bit would have to be examined, which in and of itself would potentially cause a bitflip, corrupting the original bit. The device developed at Martini’s U of C Santa Barbara lab
This project is a groundbreaking way of applying physical and theoretical quantum computing because it is using the phsycial Qubit chip and a logic circuit that applies quantum theory as an algorithm. The results being a viable way of storing data prove that several otherwise untested quantum theories are real and not just logically sound. Ideas in quantum theory that have been pondered for decades are now proven to work in the real world!
Martinis Lab will be continuing it’s tests in effort to refine and develop this approach. While the bit flip errors seemed to have been solved with this new design, there is a new type of error not found in classical computing that has yet to be solved: the phase-flip. Phase-flips might be a whole other article and until Quantum physicists solve them there is no rush for the layman to understand.
The team is also currently running the error correction cycle for longer and longer periods while monitoring the devices integrity and behavior to see what will happen. Suffice to say, there are a few more types of errors than it may appear, despite this breakthrough.
As if there was any doubt about funding…. Google has approached Martinis Lab and offered them support in effort to speed up the day when quantum computers stomp into the mainstream.
|
Jonathan Howard
Jonathan is a freelance writer living in Brooklyn, NY |

Going online without understanding the basics of how the internet works is like getting behind the wheel without knowing the road rules: you might still get where you’re going, but you could be a danger to yourself and those around you.
Using the internet is now a daily activity for most Australians. Yet, the number of people who actually understand the internet’s mechanics is small. Government and schools do work to promote cyber security and cybersafety, but the message is still not getting widespread attention.
Ultimately there is only so much that government or businesses can do to keep us safe online. At a certain point, we need to take personal responsibility and educate ourselves about how to use the internet safely.
A recent book on “cyberpsychology” and new media highlights the reasons why there has been a lag in awareness of cyber security. Much of it comes down to changing attitudes of internet users.
Various studies have shown that there is a general lack of understanding about how the internet actually affects us. This is particularly the case since the advent of Web 2.0, whereby we started posting user-generated content to the internet, some of it of a private nature.
Internet use has evolved quickly, and the rate of adoption of new applications has been phenomenal, outstripping the pace of regulation or research into internet use. When cars started hitting the roads in the early 20th century, they didn’t change nearly as rapidly, and governments responded quickly through regulation and promoting new road rules.
While some of us are aware of the dangers of the internet, the idea that “it won’t happen to me because I am not doing anything ‘dodgy’” is a common fallacy. Car owners have insurance because they know that even if they drive carefully, they do not have full control of the environment and other drivers.
There is also a generally low level of digital literacy, including basic things like knowing how a web browser works, what sources to trust and where uploaded information is stored.
This low level of digital literacy also contributes to the attitude of some parents and teachers, who proclaim it’s impossible to keep up with their children. Therefore cyberspace is seen as the domain of so called “digital natives”. Conversely, parents are able to instruct their children when they hop in the driver’s seat.

Michael Summers/Flickr, CC BY-NC-ND
Some people may also divest personal responsibility when it comes to cybersafety, preferring to trust government, via regulation, or business, through their own security policies, to protect them. Or they hope that their work or school will set up adequate firewalls.
This is problematic in that it is us who have final control in what we seek out, download, share or allow access to. Ultimately, firewalls are useless if the we freely provide the sensitive information to those who would misuse it.
In Australia there is a relatively strong culture of privacy and confidentiality. An example of this is shown by the resistance to a national smart card even just for health reasons, and the national identity card.
This Australian interest in protecting privacy could to be harnessed to stimulate more widespread interest in cyber security more broadly.
However, it is important to understand the limits of Australian privacy laws and appreciate that it can be difficult to administer such laws. The internet does not have clear national boundaries making Australian laws potentially limited as most of us access sites internationally.
Christopher Kuner, a lawyer at Hunton & Williams, has written a concise summary of the progress of privacy laws internationally.
And just as a driver should know their vehicle and its limitations, we should know the basics of our browser settings and the privacy settings of any apps and software we might be using. In addition, as more are using the cloud, they should also be aware of the conditions of using these services. After all, most drivers carefully pick the mechanic who services their car.
There is also a need for us to be aware of what we are sharing online. More importantly, with whom we are sharing it. It is easier than ever for strangers to get to know us just by looking at what we share through social media. Disparate pieces of information, even from different sites, can be pulled together to form a picture of us, making us an easier target for things like identity theft.
Finally, we should be aware of unfamiliar websites and the possibility of Trojans, malware and phishing scams.
Usually a simple Google search will yield a lot of information on how we can minimise these kinds of threats. Google itself also has pages of useful information on online safety. We don’t hand over our car keys to strangers, or let others know publicly where we keep them. Neither should we freely allow access to our personal devices or our private information.
Government regulation and business protections alone are not sufficient to keep us safe online. Just like on the roads, it also takes a measure of personal responsibility and a commitment to learn the basic skills required to use the internet to keep ourselves, and those around us, protected from online threats.
![]()
This article was originally published on The Conversation.
Read the original article.