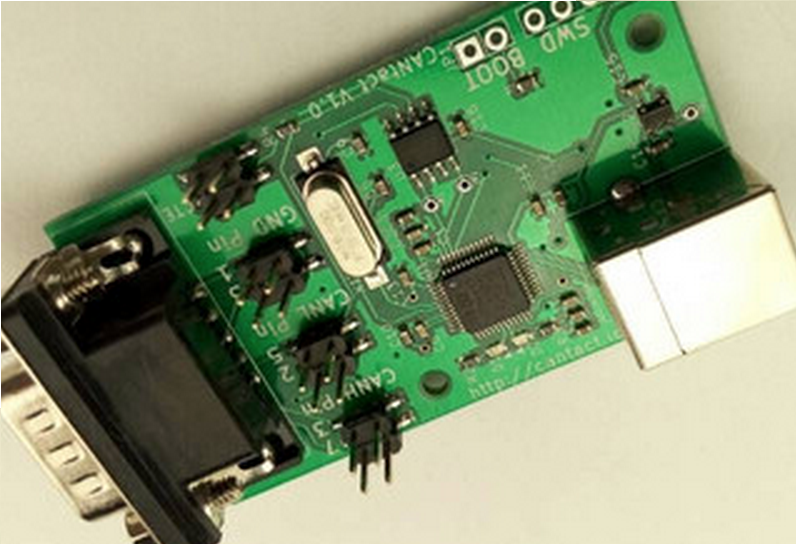
Right now, Eric Evenchick is presenting CANtact at Black Hat Asia 2015 security conference in Singapore. Cantact is a hardware interface that attaches to the car’s CPU at one end and a regular laptop at the other. He’s already figured out how to do several simple hacks. It may sound like a simple device but the pricey commercially-available on-board CPU interfaces have been a consistent obstacle to car security research.
Car Companies have a huge security hole that they have not publicly addressed. The only reason people don’t regularly computer hack motor-vehicles is a lack of commercially available hardware. Hacking a car’s electronic system is something only a few people would even have the equipment to learn. To become a specialized security researcher in this area you would have to have a car you are willing to seriously mess with, which is expensive in and of itself. Some people might have access to a clunker that was made recently enough to have a CPU but they can’t afford the $1,200 stock cable that your local car mechanic would have to run the pre-fab software provided my the manufacturer. Eric Evenchick spent the last year figuring out exactly what makes the hardware tick, so he could put it int he hands of security researchers for the price of a dinner at a fancy restaurant.
24-year-old Eric Evenchick calls the controversial device CANtact, and he’s going to present it today at Black Hat Asia security conference in Singapore, whether car companies like it or not. The code that comes on the board attached tot he cable is open source. He can get it as cheap as $60 and maybe it will sell through third parties for $100. CANtact uses any USB interface to adapt to a car or truck’s OBD2 port at the other end. OBD2 ports usually connect under the dashboard and talk to the car or trucks CPU. In most modern vehicles, the complicated Controller Area Network, or CAN, controls the windows, the brakes, the power-steering, the dashboard indicators and more. It’s something that can disable your car and most people shouldn’t mess with it just yet. Once peer-collaborated info breaks into the mainstream, Evenchick hopes customized CAN systems will be common practice.
“Auto manufacturers are not up to speed. They’re just behind the times. Car software is not built to the same standards as, say, a bank application. Or software coming out of Microsoft.” Ed Adams at Security Innovation, 2014
Is can hacking a security threat we’ll see in the future? Quite probably. Back in 2013 security researchers Chris Valasek and Charlie Miller used DARPA funding to demonstrate how possible it really is to affect steering and brakes once the CAN system is accessed.
In the controversial death of journalist Michael Hastings, some people suspected car-hacking. It’s never been proven but you can read a detailed examination of the evidence in the Cosmoso.net article: Revisiting the Death of Michael Hastings
Evenchick is not trying to allow hackers to more easily hack cars. Instead he claims more affordable gadgetry will improve security, which seems to be the way tenuous relationship of security culture and hacking has always gone. In the test described in the link to the forbes article above, Valasek and Miller rewired a $150 ECOM cable to access and test vehicles’ OBD2 ports. CANtact comes out of the box ready to do what Valasek and Miller had to stay up late nights perfecting.
Anyone who attended Black Hat Asia, or can get a hold of any video of Evenchick’s presentation can contact Jon Howard: [email protected]
|
Jonathan Howard
Jonathan is a freelance writer living in Brooklyn, NY |